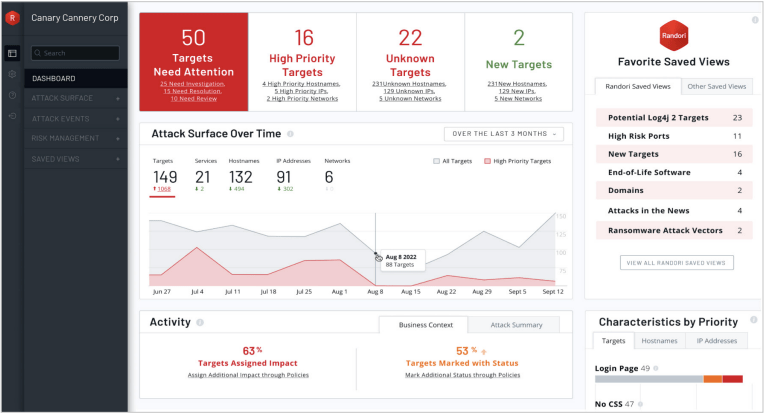
See your attack surface like an attacker
To know where attackers will strike, you first need to know how they view your attack surface. IBM® Security Randori Recon provides continuous asset discovery and issue prioritisation from an attacker’s perspective.
With cloud migrations, shadow IT, and mergers and acquisitions (M&A), your perimeter is constantly changing. These changes represent windows of opportunities for attackers. Discover them with Randori Recon – no installation or configuration required.
Just like real threat actors, Randori Recon continuously monitors your external attack surface, uncovering blind spots, misconfigurations and process failures that would otherwise be missed. Using a black-box approach, Randori finds the Internet Protocol version 6 (IPv6) and cloud assets that others miss.
Key benefits:
- Discover your unknowns
View your perimeter like an attacker to expose misconfigurations and process failures. No installation required - Prioritise your findings
Pinpoint an attacker’s top targets with the patent-pending model built on hacker logic - Reduce your attack surface
Stay a step ahead of shadow IT, M&A, and unexpected change. Alerts inform you of new risks as they arise
Discover the most tempting targets in your environment available; try our free attack surface review. We will look at:
- Which active assets are on your perimeter
- Which are “targets” attached to potentially attackable software
- Which are “top targets” that are highly tempting to an adversary
There’s no work required. We simply take your email domain to seed the platform and get results. Contact us for more information.


