Our co-managed SIEM/SOC model supports resource constrained IT teams.
Our solution offers continuous environment monitoring by aggregating logs into a central location, in accordance with recommendations from the Essential Eight, ISO 27001, and NIST frameworks.
The logs, ingested from various sources, are then correlated, condensing millions of events into a prioritised set of alerts. Our years of experience serving the education sector have enabled us to develop an education-specific SIEM rule set, as well as a competitive pricing model for education customers.
24/7 SOC services with SIEM implementation
Our 24/7 SOC team, functions as an extension of your team.
When an alert occurs in the SIEM, our team notifies you promptly to address the threat.
Should the threat occur after business hours, our SOC analysts will move to contain the threat, with actions clearly defined by our Incident Response Mechanism.
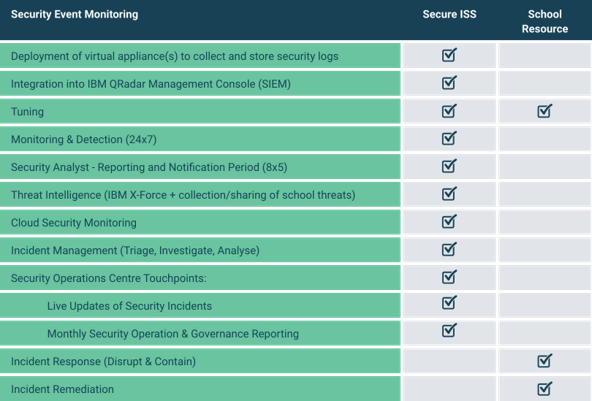
Services provided by our SOC team as part of implementing SIEM in your environment include:
- Continuous monitoring of your organisation’s environment
- Investigation and alerting of any incidents, with the ability to assist clients in response activities.
- Conducting monthly governance meetings to review your security posture.
- Providing regular SOC advisories on the current Australian threat landscape and its specific implications for schools, based on data collected from almost 100 unique environments.
IBM QRadar – The market leading SIEM
Our Security Operations Centre (SOC) is powered by IBM QRadar so when you subscribe to any of our Monitoring, Detection and Response solutions your enterprise is benefiting from:
- Security Orchestration, Automation and Response (SOAR)
- Endpoint Analytics
- User Behaviour Analytics
- Cloud Visibility
- Threat Intelligence
- Artificial Intelligence
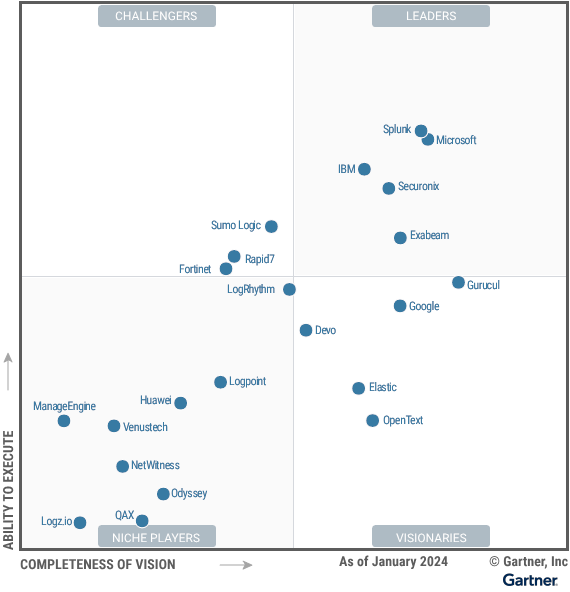
Gartner has recognized IBM as a Leader in the Magic Quadrant for SIEM for the 14th consecutive time.
This follows on the heels of IBM being recognized as a leader in the Kuppinger Cole Leadership Compass for Intelligent SIEM platforms.


