What is Privileged Access Management?
Privileged Access Management is the management of accounts, passwords, keys, files and other secrets that provide any type of privileged access to a system within an organisation’s infrastructure or across the cloud. Although the concept of management is straightforward, the organisational environment(s), business and security requirements rarely are.
Why a PAM tool assists?
PAM tools assist organisations in providing secure access to critical assets and meet specific compliance requirements. PAM tools manage and monitor privileged accounts and access to systems.
However, a toolset alone will not provide a successful outcome to a PAM project. In addition to the technology toolset (as a core), for a PAM project to be successful, it is equally reliant upon people and processes. Years of poor technology practice cannot be changed overnight! There can be significant change management within an organisation when the PAM processes and solutions are deployed. PAM projects require continued stakeholder support and sponsorship to ensure a successful journey.


In our experience, successful PAM projects are a journey that the entire organisation must embrace. They should be seen as an ongoing program of works, rather than an initial project and tool (set and forget!). PAM will permeate an organisation, affecting a number of business units and quite often-external partners and technology vendors.
As the digital transformation initiatives change an organisation (cloud, new in-house workloads etc.), so to do the requirements for the PAM implementation.
The effectiveness of the processes as they relate to PAM should be revisited on an ongoing basis, to ensure that the overall program continues to deliver on the originally agreed outcomes for the business.
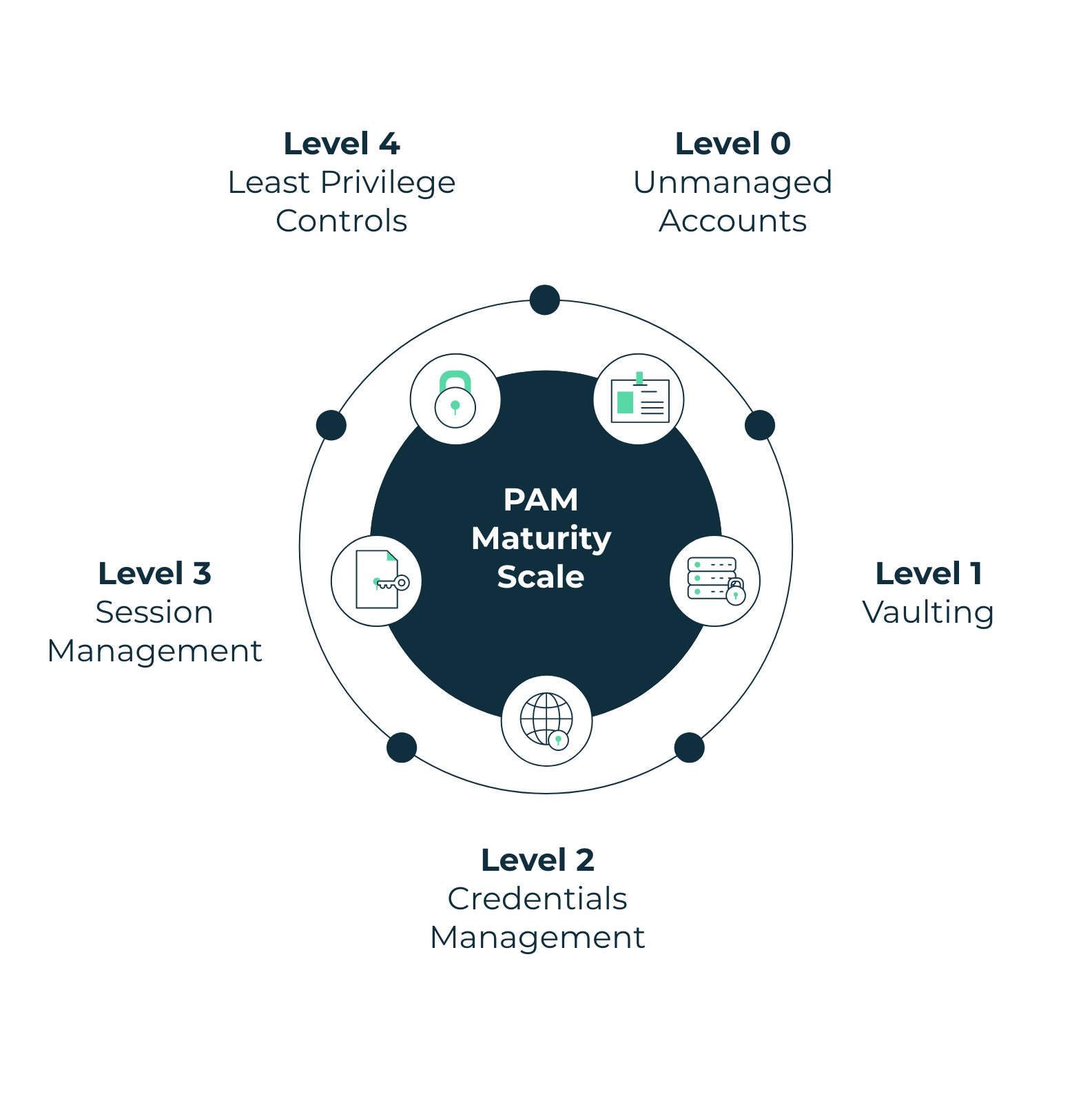
PAM Maturity Levels
When evaluating a privilege program, it can be considered against a PAM maturity scale.
Level 0 : Unmanaged Accounts – Perhaps processes in place to store privileged account passwords within the organisation
Level 1 : Vaulting – Replacing a Password Database such as KeePass or LastPass etc.
Level 2 : Credentials Management – Obfuscating Passwords from users and Rotating Passwords across an organisation
Level 3 : Session Management – Provide Audit and Recording of privileged sessions for training and breach purposes;
Level 4 : Least Privilege and removal of hard coded credentials – Introduction of least privilege controls within an organisation and removing hardcoded credentials from applications and machine to machine engagements