An organisation’s employees are often the last line of defence when it comes to an organisation’s cyber resiliency. In recent times people have become the primary attack vector for cyber security threat actors around the world, unfortunately, humans rather than technology can represent the greatest threat to organisations.
Companies MUST ensure that cyber security awareness training is provided to all employees in order to assist them in understanding their security responsibilities and help them become “cyber aware”.
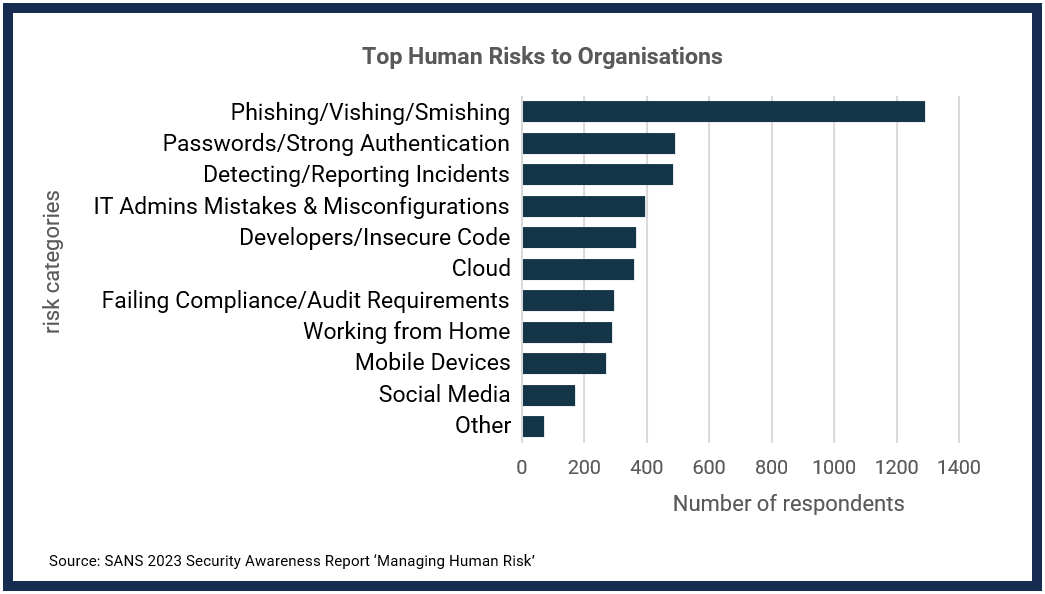
What are the top human risks to organisations?
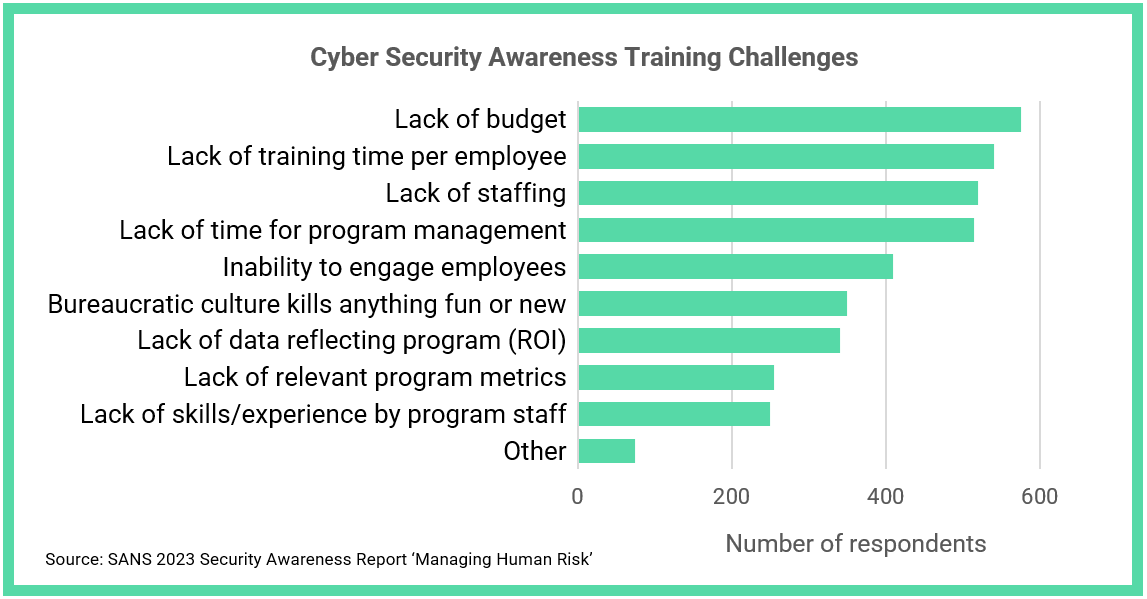
Challenges when introducing Security
Awareness Training
Secure ISS offers a cost effective and time efficient training solution that empowers organisations to be prepared for and aware of cyber threats.
Our solutions teach organisations and employees the dangers of operating in a cyber connected world, how to spot potential malware behaviours and reduce the risks associated with potential threats to the organisation. The approach is engaging, video-based training courses to ensure that concepts are retained, and outcomes can be validated through short tests and simulated phishing attacks.
The training is provided regularly and can be gamified. This assists measuring effectiveness and contributes to employee engagement.
Pricing is from $3.50 per user, per month (volume discounts apply).




