
ASD Annual Cyber Threat Report 2023 – 2024
Cost of a Data Breach Report 2024
X-Force Threat
Intelligence Index 2024
Overview of Cyber Security Obligations for Corporate Leaders


ASIC Cyber Pulse Survey 2023
ACSC’s Cyber Incident Response Plan Guidance


Cost of a Data Breach Report 2023
SentinelOne XDR Use Cases

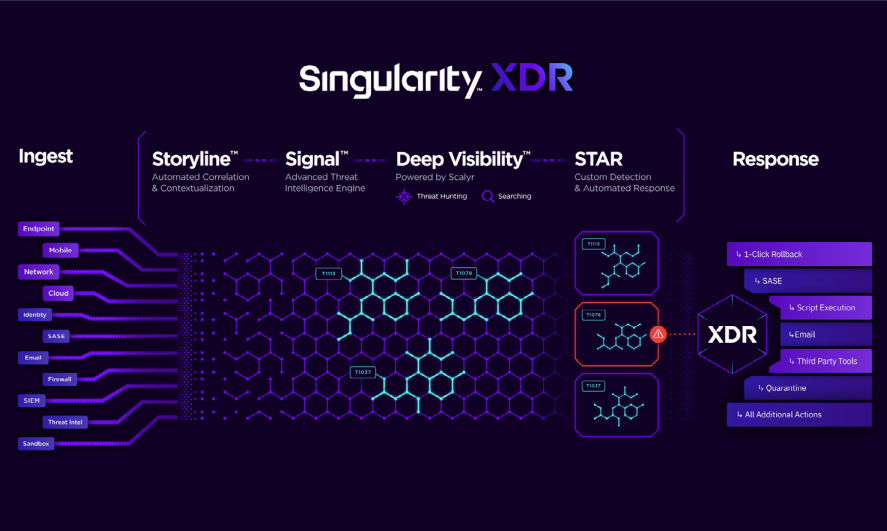
Begin Your XDR Journey with Frictionless 1-click Integrations
Landmarks on your Cyber Security Journey

X-Force Threat Intelligence
Index 2023
IBM QRadar Solution Brief


IBM QRadar SIEM Technical Review
MITRE Engenuity™ ATT&CK® Evaluation


ACSC Cyber Threat Report 2021-22
X-Force Threat
Intelligence Index 2022


IBM Security Ransomware EDR Demo
MITRE Atta&ck Evaluation – IBM Security ReaQta


Case Study: critical infrastructure
EDR Buyer’s Guide

Security Megatrends and Their Impact on
Endpoint Security
Cost of a Data Breach
Report 2022


IBM Security QRadar XDR demo
Introducing IBM Security QRadar XDR


SIEM and NDR: Better Together
Six Myths of SIEM



