What is a Security Assessment?
In its simplest form, the main purpose of the assessment is to identify the security gaps within an organisation focusing on the confidentiality, integrity and availability of data, users and systems in the environment. The auditor will look at how confidentiality is maintained by observing how authorised and unauthorised access attempts are dealt with, and how data and user information confidentiality is maintained. The auditor will also look at how the business maintains the integrity of the environment by observing different processes like the levels of privileged data and assets, how they are controlled, and by whom. The auditor will then look at how data is made available by the business and how secure that availability is to different users of that data.
The Auditor will also assess the different services within the organisation and any other service such as cloud solutions where data may reside.
The edge of an ICT environment is no longer the network perimeter, but different components like user identity, 3rd party and vendor access management, cloud applications and BYOD devices. In some instances, the list is mighty.
It is important that a business understands the gaps in its security, the control of those gaps, or lack thereof, and the risk the business incurs by not addressing those gaps.
A risk assessment takes the cyber security assessment gap findings, and a risk score is added to the findings. The focus is on regularly assessing your network edge and preventing security vulnerabilities.
We provide both cybersecurity and risk assessments of your environment to identify the security gaps, score the risk of those gaps to your business and deliver solutions using processes, toolsets and services to mitigate and control those risks.

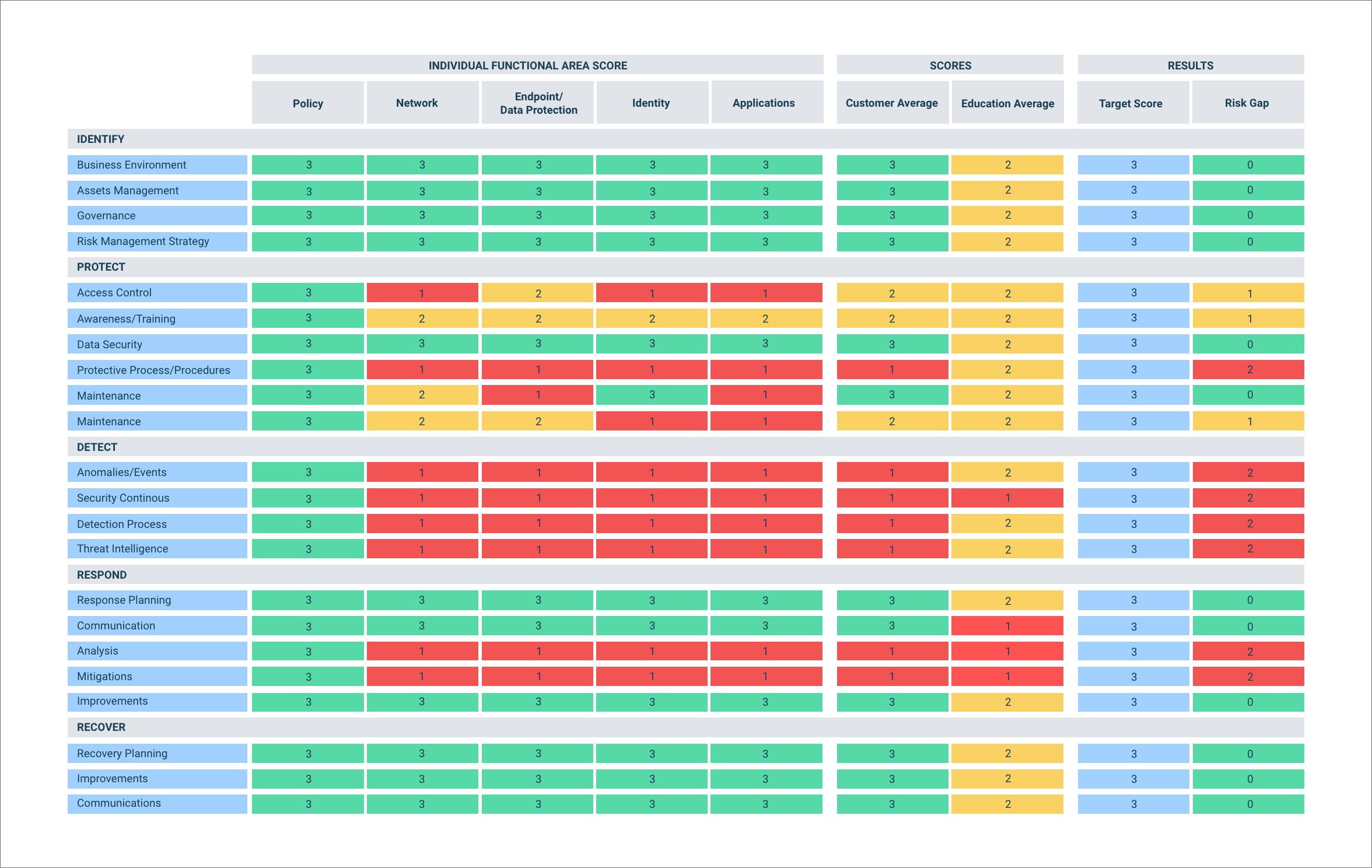
Example below of Security Assessment heat map