What is External Penetration Testing?
External Penetration Testing is a security assessment conducted through the Internet by an ‘attacker’ with no preliminary knowledge of your system. Such a test provides organisations with an understanding of how their business looks to a hacker or malicious actor on the other side of the internet. Such ‘Black Hat’ exercises are conducted with or without client management awareness.
What is Internal Penetration Testing?
Internal Penetration Testing is a security assessment with scenarios based on an internal attacker, such as a visitor with only physical access to your offices or a contractor with limited systems access. Such a test provides organisations with an understanding of how vulnerable their business is to a malicious actor that has subverted the external or perimeter defences of the business.

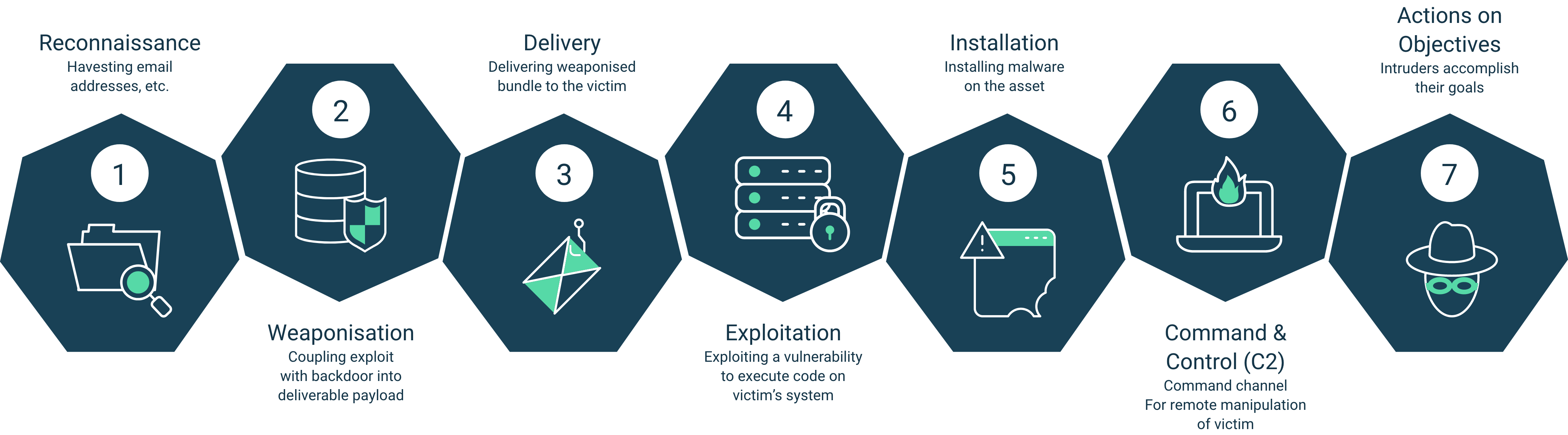
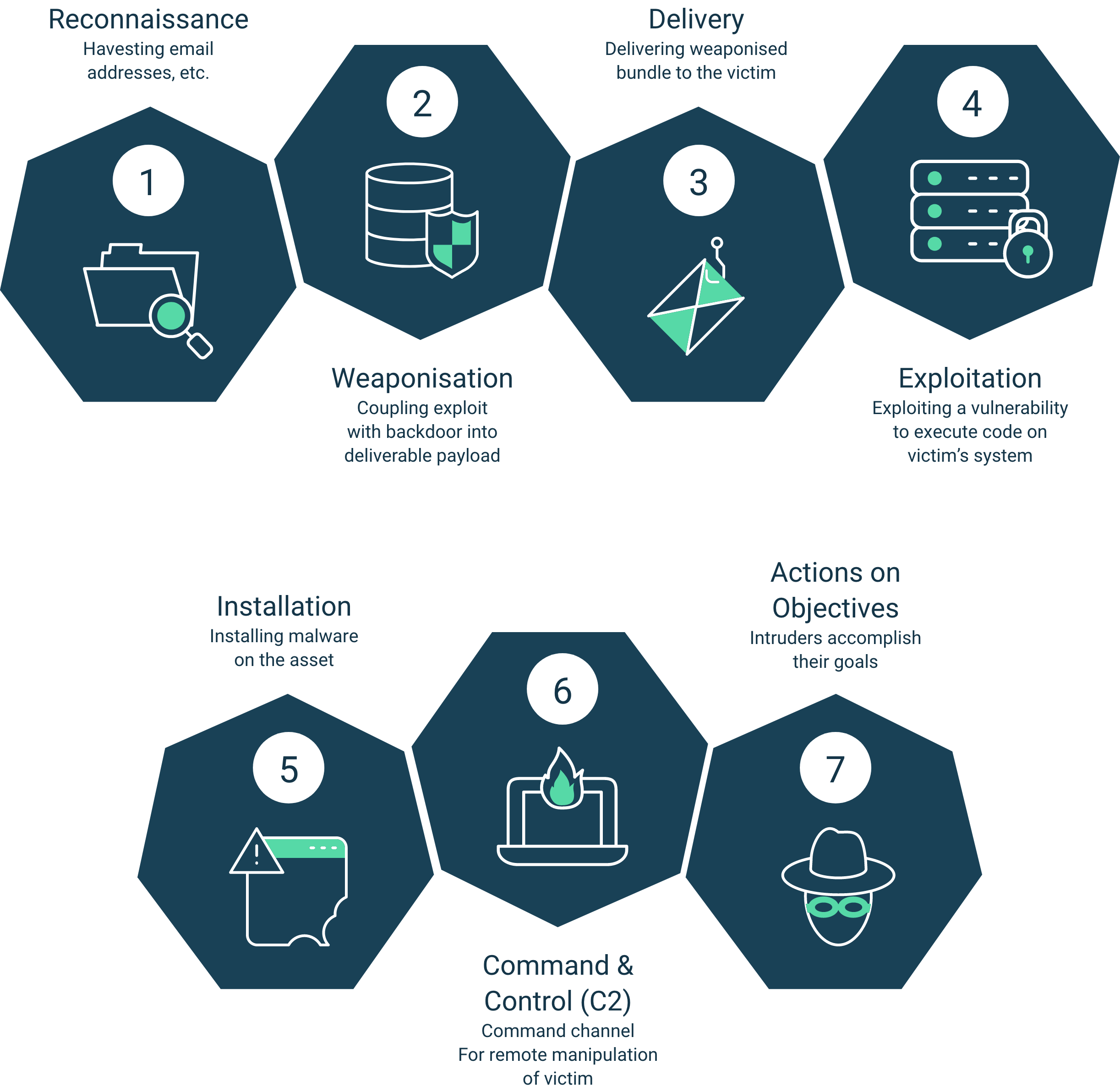

Penetration tests enable an organisation to gauge how susceptible it is to an attacker (whereby an attacker had similar access to the Penetration tester as agreed in the testing scope).
How often should penetration testing be completed?
Penetration tests should be done on a regular basis, bi-annually or annually (at a minimum) or after large infrastructure changes or security initiatives are delivered into an organisation.


