Implement continuous vulnerability scanning to stay ahead of threats
Continuous vulnerability assessment (CVA) involves continuously scanning your environment to identify vulnerabilities before they can be exploited. Cybersecurity frameworks such as Essential Eight and NIST recommend incorporating CVA as part of a comprehensive cybersecurity solution, alongside SIEM and endpoint security, to further strengthen your security posture.
What sets Secure-ISS apart for your CVA?
Our CVA platform, SecureSight, was developed in collaboration with key clients to ensure it effectively supports busy IT teams in prioritizing their task.
Unlike most vulnerability scanners, SecureSight CVA reports are designed to be easy to read and provide clear, actionable recommendations.

Management and Operation Dashboards
Reduce reporting timeframes and ensure that the program remains effective.

Filterable Datasets
A variety of datasets including network, risk, attack vector and vulnerability assets are provided to assist with quickly identifying risks and completing remediation tasks.
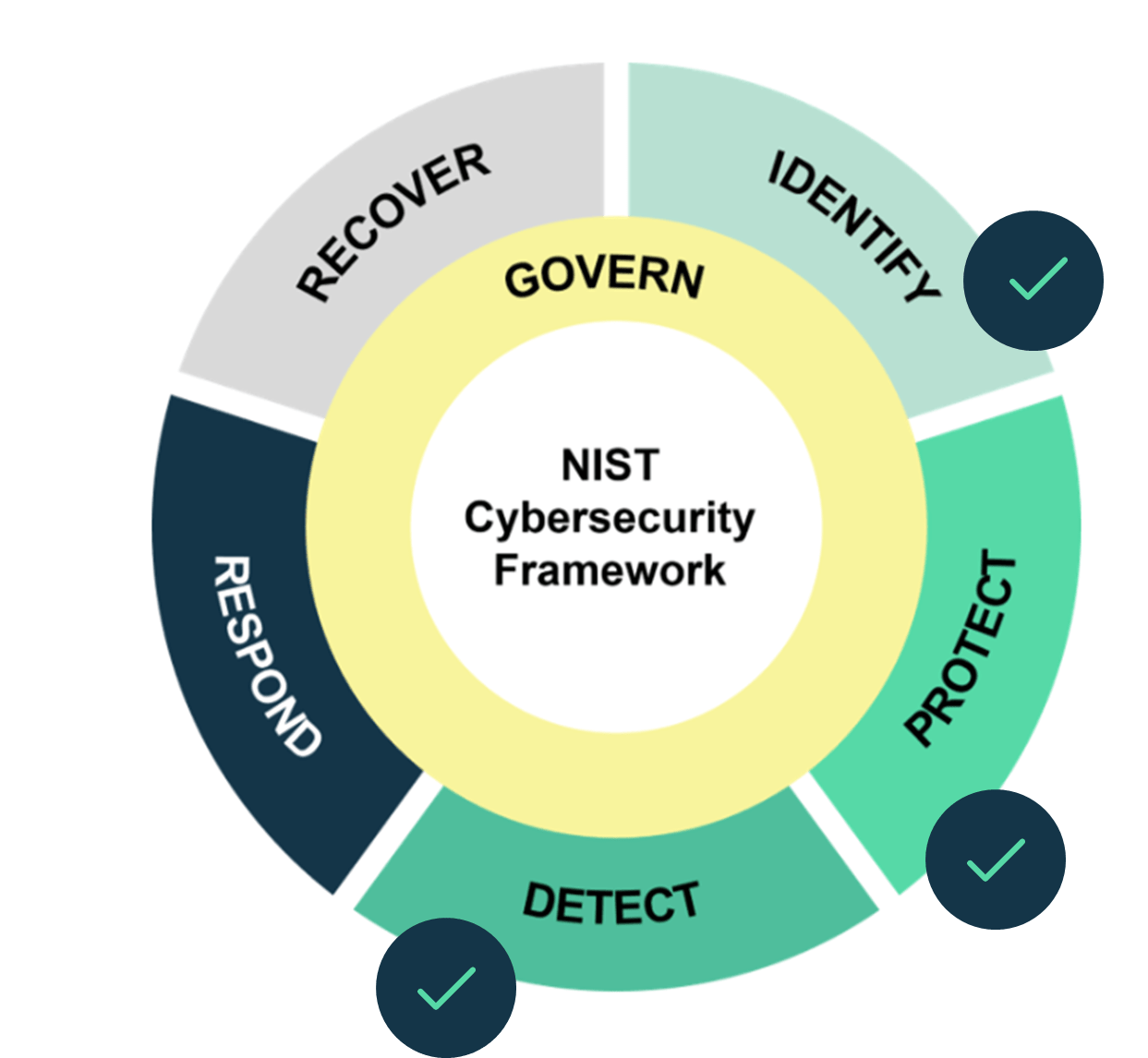
CVA is strongly recommended under both the Essential Eight and NIST 2.0 frameworks.
CVA is recommended under the Essential Eight framework for its role in enhancing the ‘Patch Applications’ strategy by continuously identifying vulnerabilities that needs patching.
It also supports ‘Patch Operating Systems’ as well by uncovering operating system vulnerabilities for remediation, ensuring that both applications and operating systems are up to date with security patches.
Under the NIST framework, CVA is also an essential component of these guidelines.
- CVA helps to identify and catalogue vulnerabilities across the environment.
- CVA also supports protection activities by identifying weaknesses that need mitigation.
- CVA directly supports this function by providing the capability to detect vulnerabilities in real time.
What are the benefits of CVA over a penetration test?
In the evolving landscape of cyber threats, a one-time security check is no longer sufficient. Many organisations are allocating their penetration testing budgets to CVA tools, which offers several benefits over a one-time penetration test report.
| CVA | Penetration Testing | |
| Outcome | Vulnerabilities that are prioritised with remediation instructions | List of vulnerabilities, no easy way to prioritise or remediate |
| Timescale | Continuous, always up to date | Static, outdated |
| Response | SIEM customers benefit from 24/7 SOC support, ensuring comprehensive security and faster alerts. | Recommended remediation actions with little detail |
How our CVA service works
- Initial consultation and training:Our team will assist you in compiling a list of IP addresses to scan and offer training on how to navigate the SecureSight platform, utilise its features and prioritize security options.
- Set up: We will assist you to deploy a vulnerability scanning engine inside your network. The set up is agentless and doesn’t require any software to sit on any devices.
- Continuous monitoring: Scanning regimens are set up in accordance with your cybersecurity goals (for example a target Essential Eight maturity level), but we generally recommend scanning server networks weekly and public assets daily. The data in SecureSight is updated daily.
- Alerts: You will receive email notifications when critical vulnerabilities (public-facing or automated exploits) are found.
- Remediation support: Our team can provide high level patching support for IT teams requiring additional assistance.