On Tuesday, January 14, 2025, security company Fortinet published an advisory on CVE-2024-55591, a critical zero-day vulnerability affecting both FortiOS and FortiProxy technologies.
Secure-ISS are calling attention to a new campaign that has targeted Fortinet FortiGate firewall devices with management interfaces exposed on the public internet.
An Authentication Bypass Using an Alternate Path or Channel vulnerability affecting FortiOS and FortiProxy may allow a remote attacker to gain super-admin privileges via crafted requests to Node.js websocket module.
Please note that this is now being exploited in the wild. A successful attack permits the threat actors to log in to the firewall management interfaces and make configuration changes, including modifying the output setting from “standard” to “more,” as part of early reconnaissance efforts, before making more extensive changes to create new super admin accounts.
Mitigations
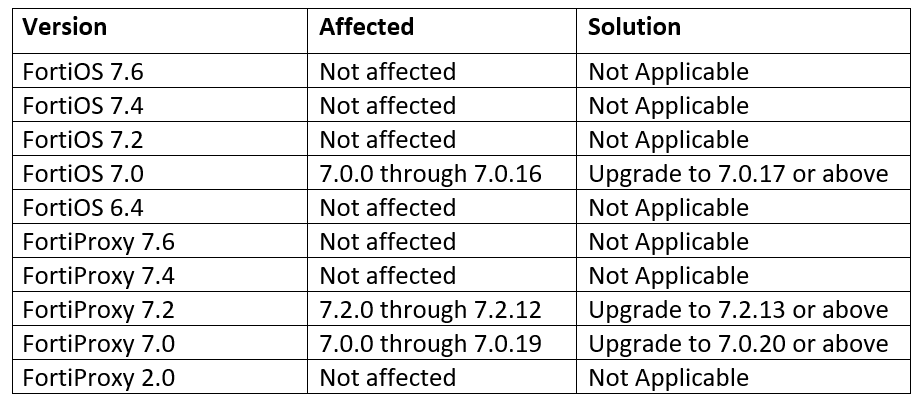
For the critical vulnerability in the section above, Fortinet has released upgrade and patching advice for affected product versions as per the table below.
Workaround
If Patching or upgrading is not immediately feasible, then consider disabling HTTP/HTTPS administrative interface or Limit IP addresses that can reach the administrative interface.
Resources
https://fortiguard.fortinet.com/psirt/FG-IR-24-535
https://nvd.nist.gov/vuln/detail/CVE-2024-55591
Sources
https://thehackernews.com/2025/01/zero-day-vulnerability-suspected-in.html


