You know you’re being talked about, on the deep web, behind paywalls, on the socials and on the Dark Web in hacker forums. We’re all paranoid, even if just a little bit!
What if you could gain an insight into how your organisation is portrayed or what is being discussed in the deepest, darkest corners of the Internet? Those areas that aren’t easily accessible.
What we can’t see (and search) can hurt us!
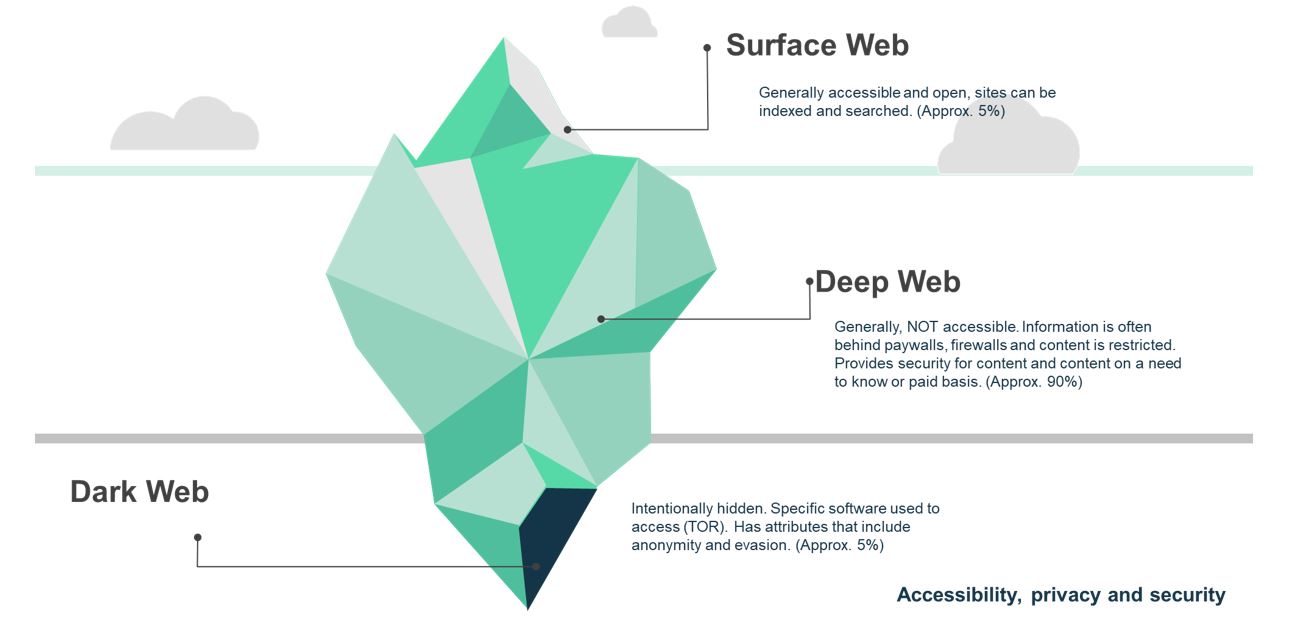
The Internet – Surface, Deep and Dark Web
External threat and reputational monitoring is a natural evolution in your monitoring regime. We can help you shine a light on these black spots, and reduce risks (be they reputational, financial/ fraud or cyber); by monitoring the deep and dark web.
- It comprises 90% of the content on the Internet
- Information is not readily available
- It is often secured behind a paywall or firewall or another authorisation mechanism.
Examples: X (Twitter), Newspapers , Media (Paywalls), Private Chat groups (Telegram), Social Media

- It was built for anonymity and evasion
- It is a natural platform for activities that various parties do not wish to have easily detected
- It is utilised for illegal, malicious and profiteering activities.
Examples: Breached/ Leaked Data, Stolen Identities, Dark Web Forums, Marketplaces, chat rooms etc.
What if there was information contained in these datasets that could…
Help you prepare for an incident; or remove that risk completely?
In relation to the Deep and Dark web, all organisations face challenges. Consider…
- How do you know if and in what circles your organisation is being discussed? (and the context, malicious or otherwise)
- What organisational data is exposed or is for sale? How does one find this data, before it finds you!?!
- Search and Hunting techniques require specialised tools and skillsets! (and don’t get us started on resources!)
- The landscape, malicious actors and attack techniques are moving with ever greater velocity. How does one stay on top of; prioritise and action any information that does come to hand?
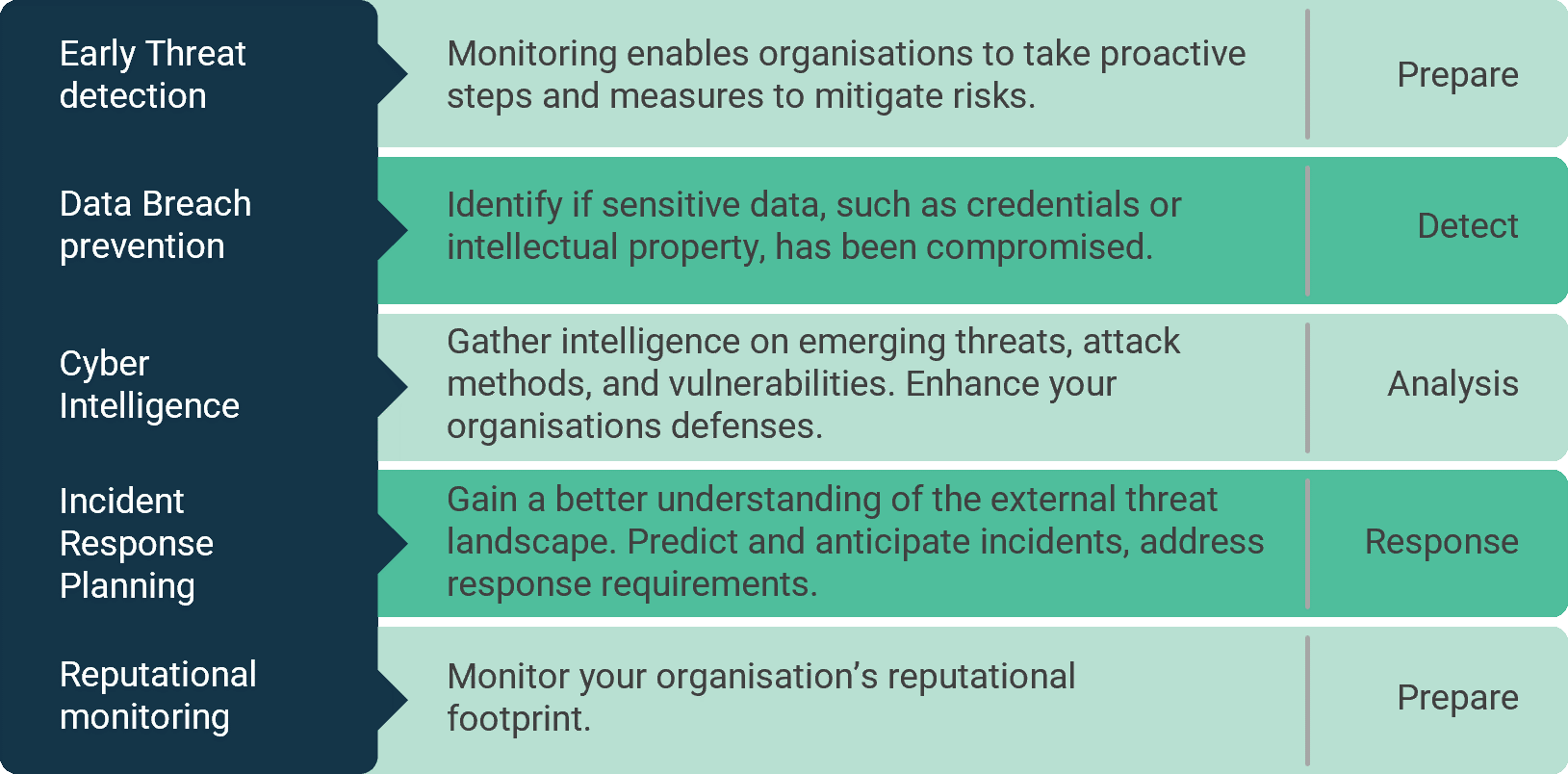
Visibility through Deep and Dark web Monitoring
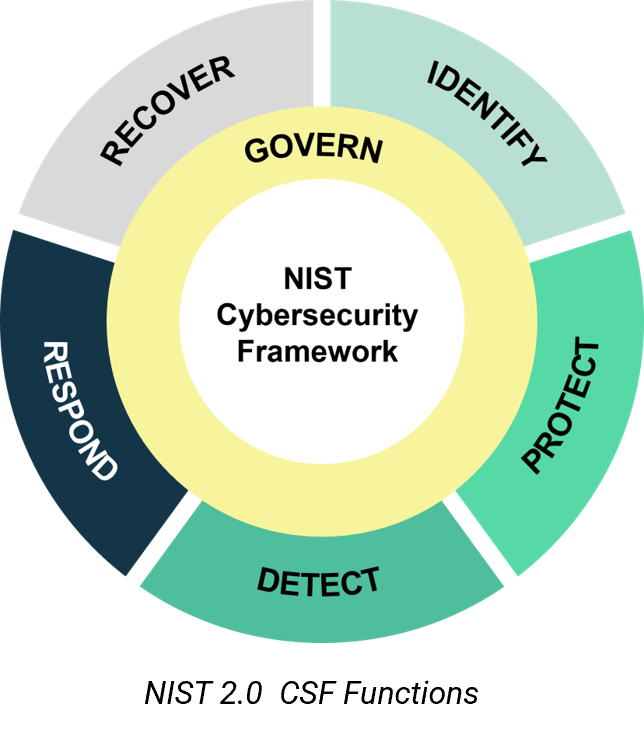
The monitoring aligns with the NIST 2.0 Cyber Security Framework:
IDENTIFY
Understand what type of information about your organisation is available on the web, to better predict and anticipate cyberattacks, fraudulent activities and become aware of risks
PROTECT
Have visibility and knowledge to implement safeguards or controls to better protect critical digital assets and data from external threats
DETECT
Detect if sensitive data has been compromised or if malicious activity targets your organisation
RESPOND
Have ability to contain the effects of cybersecurity incidents. Predict and anticipate incidents, address response requirements